Members of Congress have proposed a bill to prevent the use of contraband mobile phones in prison. This measure, initiated by Senator Tom Cotton (R-AR) and Senator Lindsey Graham (R-SC), allows state and federal prisons to use mobile phones to interfere with the system. House members David Kustov (R-TN) and William Timmons (R-SC) introduced a […]
Read MoreIt is illegal to use personal jammers in public
Mark asked: “Is there a device I can use at home, everyone can eat, I can toggle the switch, turn on something, it will cut off all cellular signals in my house. Or in a certain area, so much so No one pulls out the phone and checks Instagram or something? “, Because they all […]
Read MoreThe jammer is comparable to a small-scale nuclear bomb
Arexis jamming pods have the ability to filter through the intelligent use of DRFM jamming techniques (such as smart noise, false targets) and thereby protect the entire strike formation against low frequency radar approaches and deviations. Consistency and various saturation techniques. But the service still keeps MAPS in the background. The goal is to develop […]
Read MoreWiFi jammers will become more common in the coming years
The full name of WIFI is Wireless Fidelity, but the correct wording should be “Wi-Fi”, but we usually abbreviate it as “Wifi”. This is wireless LAN technology. Wireless routers, wireless mice, wireless keyboards, drones, etc. are very common in our lives, and are all used for WIFI connection. In 1999, when the person in charge […]
Read MoreShould jammers be used in public?
The wifi jammer will send a predefined white noise signal within a specific bandwidth, thereby interrupting all wifi / Bluetooth communication. Our scrambling unit can be programmed to scramble any number of discrete frequencies within its RF functional range. For a basic wifi interference system, the effective interference radius is about 20 meters. Jammers also […]
Read MoreDoes the prison really have smugglers?
Historically, crimes committed by prisoners have always existed in prison, such as stabbing or illegal smuggling of cigarettes. However, phones with Internet access now allow unlimited range. For example, last year, five South Carolina detainees were charged with blackmailing 442 soldiers. Prisoners use mobile phones in prison, claiming to be women at dating sites, flirting […]
Read MoreJammers can prevent students from being scammed
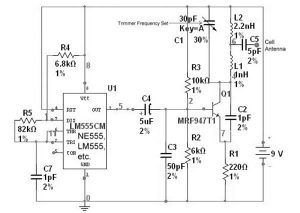
Mobile phone jammers sound like this. Devices designed to prevent the transmission of mobile phone signals or interfere with the reception of mobile phones. Their role is to generate interference within the frequency range used by the mobile phone, thereby disrupting the communication between the mobile phone user and the mobile phone signal tower. But […]
Read MorePortable adjustable mobile phone signal jammer brings comfort and health
Are you looking for a portable 3G 4G mobile phone signal jammer that can help you avoid all kinds of trouble? As we all know, with the development of mobile phone technology in the information age, people’s lives are getting busier. Sometimes we just want to play in a quiet environment. In order to make […]
Read MoreHow do different signal jammers achieve conversion
Frequency jammers try to interrupt communication signals of different frequencies, thereby preventing many wireless devices from communicating correctly. Due to the saturation of noise in the frequency, the jammer can use a 3G mobile phone network, Bluetooth, GPS, radar or infrared reader to put the system aside. According to Spanish law, the use of these […]
Read MoreJammers can also achieve counterfeiting
According to a study by the Advanced Defense Research Center, the Russians are hijacking the global navigation system on a large scale to chaotically displace thousands of ships and aircraft in their places of residence. Law enforcement, transportation, airlines, power plants, your phone, and everything that relies on GPS time synchronization and location are vulnerable […]
Read More